How Do Organizations Manage Vulnerabilities?
We must have suitable rules and architecture in place to organize and limit security vulnerabilities in an organization. Organizations typically use tools like JIRA and bug bounty programs like HackerOne to detect, classify, and remediate vulnerabilities before they can move on to the next step. A vulnerability must be addressed as soon as possible to avoid potential breaches. Vulnerabilities are managed differently by every organization.
Why Is Vulnerability Management Used?
The term “vulnerability” refers to a system flaw that allows an attacker to gain access to a system. After gaining access to the system, they can steal data, alter resources, or do a host of other actions. This is why it is necessary to track and fix vulnerabilities. If an organization is not able to patch the vulnerability on time, it may lead to the organization’s systems being breached or hacked.
For this reason, organizations establish a vulnerability management system in which they manage vulnerabilities brought to their attention either via their bounty program or by employees or their security system.
Stages of Vulnerability Management
Vulnerability management can be divided into four stages, each of which helps in the proper identification and mitigation of vulnerabilities. Let’s have a look at these stages:
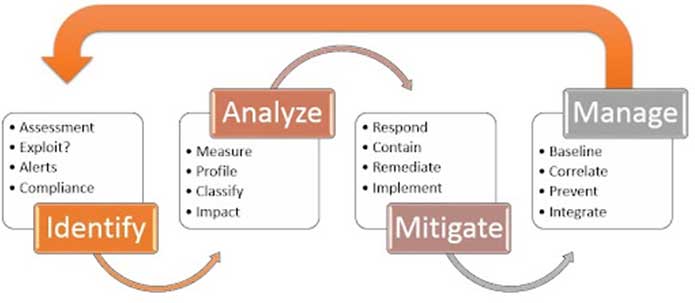
Identification
In this step, companies identify vulnerabilities that can have an impact on the organization’s operations. When a vulnerability is discovered, either internally or through a bug bounty program, the team must first determine its severity, with high or critical severity vulnerabilities receiving immediate patching.
During this phase, the security team of the organization digs deeper to determine which assets are affected, where they are located, how they can be accessed, and what protections are currently in place. The organization will be able to prioritize remediation as a result of this research.
Evaluation
The team determines the appropriate severity of the vulnerability or threat to the organization after reviewing the affected resources and current protection. The team will now know where to put their efforts and how to address the vulnerability quickly, lowering the risk as rapidly as possible. Usually, the team tackles the critical/high vulnerability first.
Multiple systems, such as the Common Vulnerability Scoring System (CVSS), are available for use by teams to determine the severity of a security vulnerability. It is critical to examine all relevant criteria, such as threat intelligence, business risk, and affected assets, to decide the severity.
Remediation
In this phase, the team will fix the vulnerability according to its severity, with critical vulnerabilities being remedied first, followed by high vulnerabilities, and so on. The team can then retest those assets to see whether the vulnerability has been exploited by anyone. As a result, the team will be able to verify that the patch has successfully mitigated the issue.
Occasionally, the team will attempt to circumvent these patches by employing one or more of the bypassing vectors to confirm that the root cause of the vulnerability has been addressed. Usually, this is done if the security team is unable to circumvent the patch.
Reporting
Once a vulnerability has been identified and remedied, organizations typically create a document that contains all the analysis performed, the types of patches that were implemented, the reasons they were implemented, the lessons learned by the organization as a result of the vulnerability, and the strategies employed to minimize similar situations in the future.
When a vulnerability is reported, it demonstrates accountability towards vulnerability detection. Similarly, when the vulnerability is patched, it shows responsibility towards vulnerability mitigation.
Conclusion
Vulnerability management can be implemented in several ways, including creating vulnerability management databases. The system’s response is determined by the organization’s immediate needs. Lesser-known vulnerabilities may not be prioritized appropriately because the team is often focusing on other projects.
Thus, a vulnerability management system and a patch prioritization mechanism help prevent less-critical vulnerabilities from falling through the cracks. It also protects the organization from being exploited.

